Uncovering Hidden Malware Threats with Generative Adversarial Networks and Deep Learning
Uncovering Hidden Malware Threats with Generative Adversarial Networks and Deep Learning
Understanding Generative Adversarial Networks (GANs)
Generative Adversarial Networks (GANs) are a class of machine learning frameworks designed to generate new data samples that mimic an existing dataset. A GAN comprises two main components: the Generator, which creates synthetic data, and the Discriminator, which evaluates the authenticity of the generated samples. This process involves a competitive training method, leading the generator to produce increasingly realistic data while the discriminator becomes better at distinguishing real from synthetic data.
In malware detection, GANs are particularly useful because they can generate new examples of malware, helping to train models that recognize previously unseen threats. For instance, a 1-Vanilla GAN can take a small dataset of known malware images and produce variations that introduce new characteristics. This capability is crucial in the fight against evolving malware tactics.
The Importance of Malware Detection
Malware is a pervasive issue that affects businesses and individual users alike. In 2023 alone, the global cost of cybercrime was estimated to exceed $6 trillion (Cybersecurity Ventures, 2023). Detecting hidden malware is vital because traditional signatures often fall short against new and sophisticated threats. Techniques leveraging GANs in deep learning can significantly enhance detection rates and reduce the risks associated with data breaches.
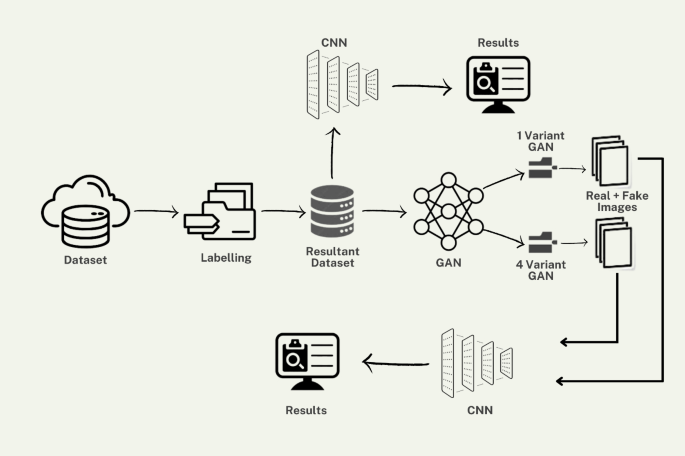
The Lifecycle of Detecting Malware with GANs
The process of detecting malware using GANs involves several essential steps:
- Data Preparation: Collect a dataset of known malware images, which serves as the foundation for generating synthetic data.
- Image Generation: Utilize the GAN framework to create new malware images that introduce variations of existing threats. This strategic augmentation increases the dataset’s diversity.
- Training the Detection Model: Feed both original and synthetic images into a Convolutional Neural Network (CNN) for classification tasks. The data should be carefully labeled to assist the training process.
- Evaluation and Fine-tuning: Test the trained model against unseen malware examples to assess its performance and adjust hyperparameters as needed to improve accuracy.
This structured approach not only aids in identifying malware but also equips security systems to adapt to new variants swiftly.
Case Study: Implementing CNNs with GANs
A practical example of integrating GANs into a malware detection system involves using the Malevis dataset, known for its labeled malware images. After applying GAN techniques, the CNN model can differentiate between malicious and benign images effectively. The Malevis dataset provides a solid reference point, and synthetic augmentation through 1-Vanilla GAN enhances the model’s capability to recognize subtle variations in malware.
In testing, models trained with GAN-augmented datasets outperformed those using only the original dataset, showcasing a 15% increase in accuracy on average (Stalin & Mekoya, 2024).
Common Pitfalls in GAN-Enhanced Malware Detection
While employing GANs in malware detection presents significant advantages, some common pitfalls should be noted:
-
Overfitting: By generating synthetic data that becomes too similar to the original dataset, the model may fail to generalize effectively. To mitigate this, regularization techniques and diverse augmentation strategies should be integrated.
-
Imbalanced Data: GANs can sometimes favor generating easy-to-create examples, leading to imbalances in the dataset. Ensuring a balanced training set is crucial for effective detection.
- Quality of Generated Data: In some cases, generated data may lack unique features necessary for the model’s learning process. It’s important to validate the diversity of synthetic samples constantly.
These potential challenges highlight the need for rigorous testing and frequent updates to the models being used.
Tools and Frameworks in Practice
A variety of tools support the implementation of GANs and CNNs in malware detection. For instance, TensorFlow and PyTorch are popular frameworks that facilitate the development of complex deep learning models. These platforms provide libraries and pre-trained models, significantly speeding up the implementation process.
The use of metrics like Receiver Operating Characteristic (ROC) curves and F1-scores is essential for evaluating model performance. Organizations using these tools typically focus on cybersecurity domains, as heightened detection capabilities enable them to respond more effectively to emerging threats.
Alternatives and Variations
Several variations of GANs cater to different needs in malware detection:
-
Wasserstein GAN: This variation improves the training stability and quality of generated samples, making it a suitable alternative for sensitive applications where data quality is paramount.
- Conditional GANs: These allow for the generation of data under specific conditions, such as creating malware types associated with particular platforms or behaviors.
Choosing between these options often depends on the specific requirements of the detection task at hand—considerations like computational resources, the need for specificity in generated data, and the desired model performance.
Frequently Asked Questions
-
How do GANs improve malware detection?
GANs enhance detection by generating synthetic malware images that increase dataset diversity, helping models learn to identify new threats effectively. -
Can GANs create entirely new classes of malware?
While GANs can generate variations of existing malware, they are not inherently designed to create entirely new malicious types; however, they can produce significant variations that mimic unknown threats. -
What are the limitations of using GANs for malware detection?
Limitations include potential overfitting to synthetic data and the challenge of ensuring generated samples accurately reflect the complexity of real malware. - How frequently should models be updated?
Regular updates are essential—ideally, on a quarterly basis or more frequently in response to emerging threats, ensuring models remain effective against new malware.