“Hybrid Deep Learning Framework for Detecting Distributed Denial of Service Attacks Using Recursive Feature Elimination”
Hybrid Deep Learning Framework for Detecting Distributed Denial of Service Attacks Using Recursive Feature Elimination
Understanding Distributed Denial of Service (DDoS) Attacks
A Distributed Denial of Service (DDoS) attack aims to overwhelm servers, services, or networks, rendering them unavailable to legitimate users. This threat has gained urgency as the reliance on digital infrastructures grows. For instance, consider a heavily trafficked online retail site during a holiday sale. If a DDoS attack occurs, potential customers may face delays or inability to complete purchases, resulting in lost revenue and disgruntled customers. Addressing DDoS threats is critical to maintaining service availability and protecting business reputations.
Key Components of the Hybrid Deep Learning Framework
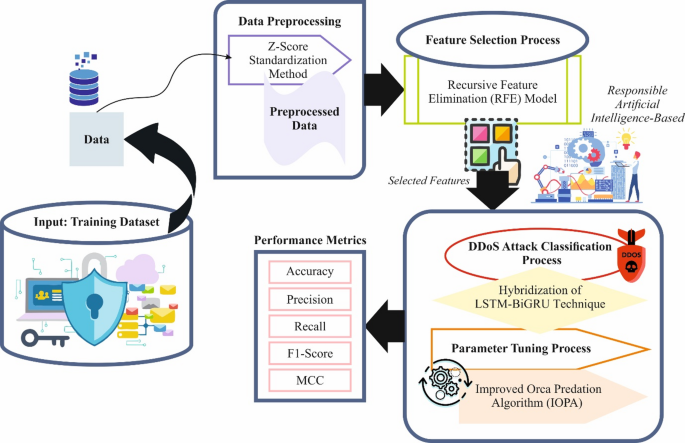
The Hybrid Deep Learning Framework comprises several core components, including Recursive Feature Elimination (RFE), a preprocessing stage utilizing the Z-score method, and the hybrid Long Short-Term Memory (LSTM)–Bidirectional Gated Recurrent Unit (BiGRU) model for attack classification. These elements work in tandem to enhance detection accuracy and performance. For example, RFE selectively improves features in a dataset, while the hybrid model effectively processes sequential data to recognize intricate attack patterns, leading to better predictions.
Recursive Feature Elimination for Feature Selection
Recursive Feature Elimination (RFE) is a systematic approach for selecting important features while discarding the least significant ones based on model performance. It iteratively refines feature selection, using statistical measures to enhance computational efficiency and reduce overfitting. Imagine an artist removing unnecessary paint strokes to create a more vivid artwork; RFE cleans up the dataset to focus on critical information. This method is especially valuable in cybersecurity, where datasets can have high dimensionality. Eliminating irrelevant features can significantly boost performance in detecting DDoS attacks.
Data Preprocessing with Z-score Normalization
The preprocessing step employs Z-score normalization to standardize input data, transforming raw data into a structured format. This technique adjusts features by centering them around a mean of zero with a standard deviation of one, ensuring all features contribute equally during training. For instance, if one feature represents the number of requests while another signifies bytes transferred, Z-score normalization prevents the model from being biased toward the feature with larger numerical ranges. This uniform scaling helps algorithms converge faster, enhancing overall model training efficiency.
Dimensionality Reduction Process
RFE plays a pivotal role in the dimensionality reduction process by discarding irrelevant features while retaining the most pertinent ones. This iterative method addresses the problem of overfitting, thereby improving the model’s performance and interpretability. For instance, consider a cybersecurity dataset with numerous attributes where only a fraction influences DDoS detection meaningfully. RFE can discern the crucial features, leading to a more streamlined and efficient attack recognition process.
Hybridization of Attack Classification with LSTM and BiGRU
In this framework, the classification of DDoS attacks utilizes a hybrid model combining LSTM and BiGRU techniques. The LSTM excels at capturing long-term dependencies in sequential data, whereas the BiGRU processes sequences in both forward and backward directions. This dual processing capability enhances the model’s contextual understanding, enabling it to effectively identify complex attack patterns. Unlike traditional models, this hybrid approach adapts to temporal dynamics, improving accuracy and robustness across various datasets, especially those that may be imbalanced.
Hyperparameter Tuning Using IOPA
Intermediary Orca Predator Algorithm (IOPA) focuses on hyperparameter tuning within the framework. By leveraging a balance between exploration and exploitation, IOPA avoids local optima more efficiently than conventional tuning methods, such as grid search. This ensures optimized model performance, particularly relevant for dynamic environments like cybersecurity. For instance, if a model operates under variable network conditions, utilizing IOPA could lead to faster convergence and enhanced detection capability against evolving DDoS strategies.
Practical Scenario of the Hybrid Framework
A company implementing this hybrid framework might process real-time traffic data to identify potential DDoS attacks. The RFE would filter the incoming data streams, and the hybrid model would analyze the significant patterns in sequence data, allowing for immediate alert generation upon detection of anomalies. This process can be visualized as a proactive surveillance system, constantly monitoring network activity and adapting to new attack vectors effectively.
Common Mistakes and Solutions in DDoS Detection
A common error in using machine learning for DDoS detection is neglecting data preprocessing, leading to suboptimal feature representation and resulting in poor model performance. To avoid this pitfall, practitioners should prioritize thorough data cleaning and normalization techniques like Z-score. Moreover, selecting relevant features via RFE can mitigate overfitting, thus enhancing predictive accuracy. Addressing these elements ensures that the model learns effectively from the available data.
Tools and Frameworks for Implementation
Implementations of the hybrid deep learning framework can utilize various tools, including TensorFlow and PyTorch, for creating and training the LSTM-BiGRU models. RFE can be integrated into the preprocessing pipeline using libraries such as Scikit-learn, facilitating smooth and efficient feature selection. Evaluation metrics such as accuracy, precision, and recall become crucial during performance assessment, allowing practitioners to discern the model’s effectiveness in real-world DDoS attack scenarios.
Alternatives to the Hybrid Deep Learning Framework
While the hybrid LSTM-BiGRU model offers substantial benefits, alternative methods like Convolutional Neural Networks (CNNs) and standalone Recurrent Neural Networks (RNNs) can also be employed for DDoS detection. CNNs are efficient in domain-related tasks requiring spatial hierarchies, while traditional RNNs may serve well in handling sequential data. However, standalone models may lack the nuanced adaptability offered by the hybrid approach, particularly in dynamically evolving attack environments, thus presenting a trade-off between model complexity and performance.
FAQ
What are the advantages of using the hybrid LSTM-BiGRU model over traditional approaches?
The hybrid model leverages both the long-term dependency of LSTMs and the bidirectional processing capability of BiGRUs. This allows it to effectively recognize complex patterns in network data, surpassing traditional models in terms of accuracy and adaptability.
How does IOPA improve hyperparameter tuning compared to traditional methods?
IOPA employs an innovative approach to balance exploration and exploitation during hyperparameter optimization, leading to faster convergence and improved performance in dynamic scenarios while minimizing computational overhead.
Why is feature selection critical in DDoS detection?
Feature selection eliminates irrelevant data, improving model training efficiency and predictive accuracy. It reduces overfitting, ensuring that the model focuses on significant patterns in the data which enhances overall system performance.
What might be the challenges faced during implementation?
Common challenges include managing high-dimensional data, selecting appropriate hyperparameters, and ensuring the model adapts to evolving attack vectors. Careful attention to preprocessing and feature selection mitigates many of these issues, enhancing model robustness.