“Gold Rush or Fool’s Gold? Evaluating Generative AI Claims in Security Tools”
Gold Rush or Fool’s Gold? Evaluating Generative AI Claims in Security Tools
Understanding Generative AI in Security Tools
Generative AI refers to algorithms that can create new content, be it text, images, or code, based on their training data. In the realm of security, these tools offer the promise of automating and enhancing threat detection and response strategies. However, with immense potential comes significant scrutiny—do these claims hold up under rigorous evaluation? The relevance of generative AI in security tools is paramount; organizations are constantly seeking advanced methods to mitigate risks and protect data.
The Core Value Proposition
The core value of generative AI in security tools lies in its ability to streamline operations. By automating mundane tasks and providing insights derived from vast datasets, organizations can refocus human resources on complex strategies and decision-making. For instance, instead of sifting through logs for anomalies, a generative AI tool might identify patterns indicative of phishing attacks in real-time, saving countless hours of manual review.
The financial impact is significant as well: reducing incident response time can help avoid costly breaches. According to IBM, the average cost of a data breach was nearly $4.24 million in 2021 (IBM, 2021). Thus, tools that can effectively minimize these risks are not merely beneficial; they are essential.
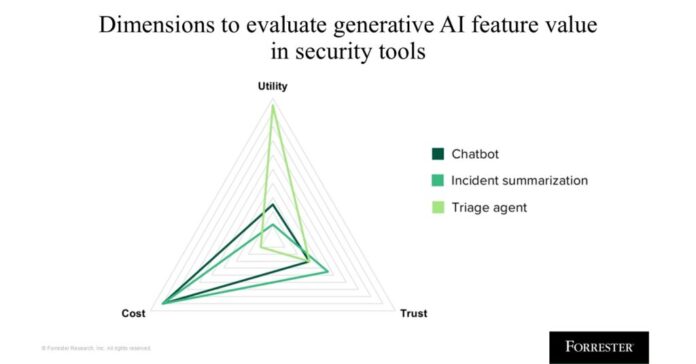
Evaluating Trustworthiness: Key Components
To assess the effectiveness and reliability of generative AI in security tools, three primary dimensions must be considered: accuracy, explainability, and security protocols.
Accuracy and Repeatability
Generative AI systems often operate on a nondeterministic basis, meaning that they might not produce identical results from identical inputs. This unpredictability can be troubling. A notable example is the average error rate of AI chatbots, which can be wrong roughly 60% of the time (Columbia University, 2023). Such inaccuracies can introduce risks in security contexts, where even slight misjudgments can lead to catastrophic breaches.
To ensure reliable outputs, organizations should look closely at the AI vendor’s validation methodologies. Effective models usually employ a combination of methods like statistical sampling, expert validation, and the use of golden datasets for training, which serve as benchmarks against reality.
Clear and Concise Explainability
Explainability addresses the opacity of AI decisions. A fundamental challenge lies in AI’s "black box" nature, where users cannot discern how conclusions were made. Security professionals should prioritize systems that articulate their reasoning processes clearly.
For instance, a security AI tool might offer a traceable method indicating how it identified a threat. Clear explainability does more than foster trust; it enhances a team’s knowledge of threat landscapes, potentially revealing new approaches to tackle security dilemmas.
Robust Security Measures
Security remains a critical concern in deploying AI technologies. Without adequate protections, AI tools could inadvertently expose sensitive data or become entry points for attackers. Adhering to frameworks like Forrester’s AEGIS (Agentic AI Enterprise Guardrails for Information Security) ensures that security protocols are embedded throughout the tool’s lifecycle.
The Lifecycle of Implementing Generative AI Tools
-
Needs Assessment: Understand specific organizational requirements and threat landscapes. This step clarifies goals for the AI deployment.
-
Vendor Evaluation: Rigorously assess potential vendors based on trustworthiness, performance history, and adherence to industry standards.
-
Pilot Testing: Initiate a small-scale implementation of the selected tool. Monitor its performance against the defined security metrics.
-
Feedback and Adjustment: Collect data on the tool’s outputs and user interactions. Adjust its deployment based on real insights.
-
Full Scale Rollout: Upon successful piloting, deploy the tool across the organization while ensuring ongoing training for the personnel involved.
- Continuous Monitoring: After implementation, continuously evaluate the AI’s performance, remaining agile to adapt to new threats and novel insights.
Common Pitfalls to Avoid
Organizations must navigate several pitfalls when adopting generative AI for security. One common issue stems from over-reliance on automation, which can lead to complacency. Incorrect assumptions about an AI tool’s infallibility can prompt neglect in human oversight.
Another significant risk is inadequate training for users, which hampers the effective utilization of the AI solution. Employees must be educated not just on operational procedures but also on interpreting AI outputs effectively.
To address these issues, organizations should foster an environment of continuous learning and emphasize collaboration between humans and AI systems.
Frameworks and Tools in Practice
Real-world applications of frameworks like the MITRE ATT&CK framework augment the effectiveness of generative AI tools. This resource catalogues adversary tactics and techniques, providing security teams with insights to refine machine learning models used in threat detection.
Moreover, metrics such as precision and recall become critical for evaluating AI performance. Precision reflects the proportion of true positive results over all positive outputs, while recall assesses the ability to find all relevant instances. These quantifiable measures inform organizations when assessing which tools genuinely provide security enhancements.
Variations and Alternatives
While generative AI presents significant opportunities, it’s essential to consider alternative security measures as well. For example, traditional rule-based detection systems, while less adaptable, offer more reliable outputs under specific conditions. The trade-off between flexibility and accuracy requires careful evaluation.
In essence, when deciding between generative AI and traditional approaches, organizations must weigh their specific needs against the capabilities each method offers.
The landscape of generative AI in security tools is shifting rapidly, and understanding its nuances can help organizations navigate this technological gold rush without falling into traps of misinformation. As the landscape continues to evolve, ongoing evaluation, education, and a keen focus on security will dictate which tools stand the test of time.