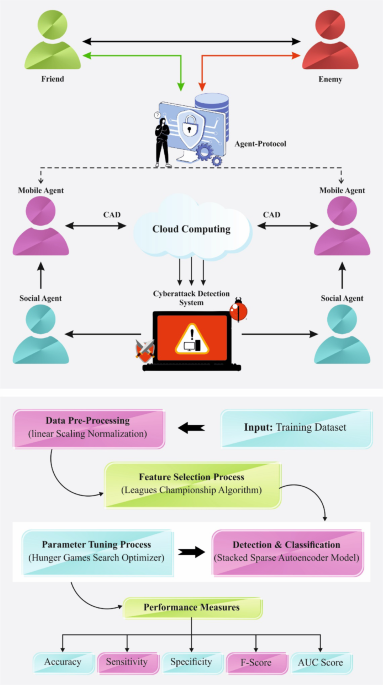
Securing the Digital Ecosystem: The CLAFS-ODLCD Model
In the rapidly evolving digital landscape, safeguarding systems against cyber threats has become paramount, especially in the Internet of Things (IoT) framework. This is where the CLAFS-ODLCD model steps in, proposing a revolutionary approach to recognizing and classifying cyberattacks within IoT infrastructures.
Overview of the CLAFS-ODLCD Technique
The CLAFS-ODLCD methodology emphasizes a structured approach to cybersecurity by integrating several distinctive subprocesses:
- LSN-based Data Normalization
- CLA-based Feature Selection Subset
- SSAE-based Classification
- HGS-based Hyperparameter Tuning
The functionality of the CLAFS-ODLCD method is visually represented in the workflow diagram below.
Data Normalization with LSN
The initial stage of the CLAFS-ODLCD technique employs Least-Squares Normalization (LSN) for data preprocessing. This method ensures that numerical values are easily interpretable by scaling them to a specific range, often between [0, 1] or [-1, 1]. Unlike typical normalization methods that center data around the mean or median, LSN preserves the original correlations between data points.
LSN proves particularly useful in scenarios where relative differences among data points matter more than their absolute values. This approach enhances the stability and efficiency of analyses across a multitude of applications.
CLA-based Feature Selection
Next, CLA (Class League Algorithm) is utilized for optimizing feature selection. Inspired by sports league systems, the CLA operates on the principle of team formation based on generated match schedules, where teams (or solutions) compete against each other.
- League Schedule Generation: Teams are organized in a round-robin format, ensuring that each team faces each other.
- Evaluating Winning Outcomes: Winners and losers are determined based on predefined metrics of playing strength, showcasing how features perform in predicting outcomes.
This competitive dynamic aids in identifying the most relevant features, thus improving the efficiency of the classification process.
Cyberattack Detection Using SSAE
In the subsequent phase, the Stacked Sparse Autoencoder (SSAE) method is introduced for detecting and classifying cyberattacks. SSAE stands out due to its ability to learn deep hierarchical representations, capturing intricate patterns associated with various attacks.
Key features of the SSAE approach include:
- Noise Mitigation: By filtering out irrelevant data, SSAE enhances the accuracy of detection mechanisms.
- Overfitting Management: Techniques like dropout regularization and early stopping are employed to prevent the model from simply memorizing training data.
- Handling Class Imbalance: SSAE employs strategies such as weighted loss functions and data augmentation to ensure that minority attack classes are well-represented in the detection process.
The architecture of SSAE is depicted in the following diagram.

Hyperparameter Tuning with HGS
The last step focuses on optimizing the model’s performance through Hyperparameter Group Search (HGS). This approach utilizes population-based strategies to explore and refine hyperparameters crucial for model efficiency.
HGS operates through several key steps, including simulating the behavior of populations, determining fitness based on performance metrics, and refining solutions iteratively for optimal results. The technique ensures a balanced exploration of the solution space while adhering to constraints of the problem.
Moving Near Food: HGS incorporates intrinsic parameters to mimic optimization behavior and reduce the solution space dynamically:
[
\overrightarrow{Y(t+1)} =
\begin{cases}
\overrightarrow{Y(t)} \cdot (1+\mathfrak{R}m(1)), & \mathfrak{R}{1}
\overrightarrow{Z{1}}\cdot \overrightarrow{Y{a}}+\overrightarrow{S}\cdot \overrightarrow{Z{2}}\cdot |\overrightarrow{Y{a}} – \overrightarrow{Y(t)}|, & \mathfrak{R}{1}, \mathfrak{R}{2}
\end{cases}
]
Through this iterative process, HGS effectively identifies hyperparameters that greatly enhance model performance.
Conclusion
The CLAFS-ODLCD model presents a comprehensive framework for securing the digital ecosystem against evolving cyber threats. By leveraging advanced techniques in data normalization, feature selection, classification, and hyperparameter tuning, it paves the way for robust and reliable cybersecurity measures—specifically tailored for the intricate demands of IoT infrastructures.