“Enhanced Intrusion Detection in IoT Using Deep Learning and Optimized Algorithms”
Enhanced Intrusion Detection in IoT Using Deep Learning and Optimized Algorithms
Understanding Intrusion Detection Systems (IDS) in IoT
An Intrusion Detection System (IDS) is a device or application that monitors and analyzes network traffic to detect suspicious or malicious activity. In the Internet of Things (IoT), where numerous interconnected devices communicate, the security challenges multiply. For instance, a smart home with multiple IoT devices can be an easy target for attackers if not adequately monitored.
The importance of robust IDS in IoT cannot be overstated, as inadequate detection mechanisms can lead to severe consequences, including data breaches and system failures. The dynamic nature of IoT traffic and the evolving tactics of cybercriminals necessitate advanced methods for intrusion detection, thereby fostering the urgency for innovative solutions.
Key Components of an Effective IDS
An effective IDS incorporates various components that work together to monitor, detect, and respond to threats. These include:
- Data Collection: This foundational component gathers network traffic data from IoT devices, establishing a baseline for normal operations.
- Analysis Engine: This engine processes collected data using algorithms to identify anomalies or signatures of known attacks.
- Alert Mechanism: Once an intrusion is detected, this mechanism notifies users or administrators so they can respond promptly.
- Response Capabilities: To enhance security, effective IDS should also automate responses to detected threats, such as blocking malicious IPs.
Consider a security alarm system in a home; it detects unauthorized entry and alerts the homeowner, while also triggering an automatic response, such as sounding an alarm or locking doors. Similarly, an IDS is crucial for safeguarding IoT networks.
Deep Learning Techniques in Intrusion Detection
Deep learning leverages neural networks to analyze vast amounts of data. In IDS, deep learning can enhance detection capabilities by learning from historical data to identify abnormal patterns. For instance, a deep learning model can distinguish between typical device communications and those indicative of a cyber-attack.
In real-world applications, neural networks can significantly reduce false positives. A model trained on network traffic data that includes both normal and attack samples can improve the system’s ability to detect genuine threats while minimizing unnecessary alerts.
Game Theory for Balancing Data Sets
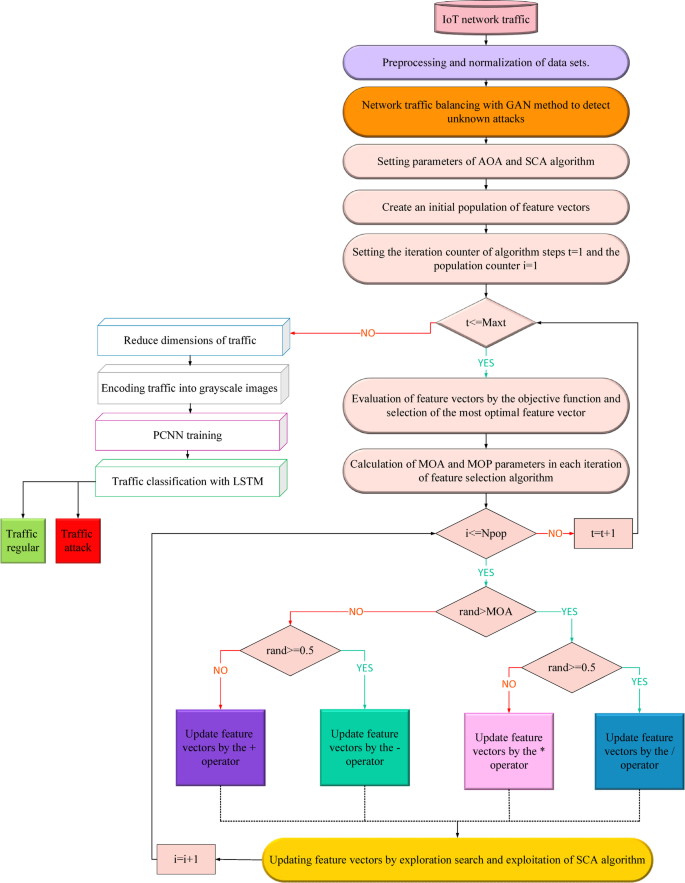
One common challenge in developing effective IDS is the imbalance between regular traffic and attack samples. Typically, legitimate traffic vastly outweighs attack data, which can skew model training. Game theory offers a solution by framing the relationship between the generator and discriminator in Generative Adversarial Networks (GANs).
Think of this like a game between two players: one generates synthetic data designed to mimic attack patterns, while the other evaluates it for authenticity. This adversarial relationship helps create a balanced dataset that simulates a more realistic distribution of attack instances, allowing models to generalize better to unknown threats.
Steps to Implement Effective IDS in IoT
The implementation of a robust IDS for IoT typically involves several key steps:
- Data Preprocessing: Cleaning and preparing the data for analysis, which includes normalization to eliminate discrepancies among features.
- Dataset Balancing: Using techniques like GANs to generate additional attack samples, thereby achieving balance in the dataset.
- Feature Selection: Employing algorithms such as the Arithmetic Optimization Algorithm (AOA) and Sine Cosine Algorithm (SCA) to filter out irrelevant data.
- Encoding Traffic Data: Transforming raw network traffic into grayscale images enables the application of convolutional neural networks (CNNs) for effective pattern recognition.
- Model Training: Utilizing the prepared dataset to train a deep learning model that can effectively classify traffic as normal or malicious.
Each of these steps is interdependent, requiring meticulous execution to ensure an effective IDS.
Common Mistakes in IDS Implementation
Many implementations falter due to overcomplexity or inadequate training data. A common mistake is failing to account for the diversity in network traffic, leading to overfitting. Overfitting occurs when the model learns to identify noise instead of actual threats, thus failing during real-time operations. Implementing robust data preprocessing and employing various augmentation techniques can mitigate this issue.
Another frequent pitfall is neglecting the ongoing need to retrain models with new data, which can lead to systems unable to recognize evolving attack vectors. Continual monitoring and updating of datasets are vital to maintaining an effective IDS.
Tools and Frameworks for IDS
Several tools can assist in building an effective IDS for IoT. Common frameworks include TensorFlow and Keras for deep learning, as they provide extensive resources for developing and training neural networks. Other tools may focus on network traffic analysis, such as Wireshark, which can help gather relevant data for feeding into an IDS.
Utilizing these tools in conjunction with specific metrics, such as accuracy and false-positive rates, allows developers to measure the effectiveness of their solutions continuously.
Potential Alternatives in IDS Approaches
While deep learning is a powerful approach, alternatives such as rule-based systems or combining traditional machine learning techniques with deep learning can offer benefits. Rule-based systems provide transparency and can be easier to interpret, while traditional models may require less computational power during implementation.
However, these alternatives can fall short in the capability to adapt dynamically to new attack patterns when they lack robust learning mechanisms. For real-world applications, a hybrid approach combining deep learning and traditional methods could balance performance and interpretability.
Frequently Asked Questions
Q1: How does deep learning improve IDS in IoT?
Deep learning improves IDS by enabling models to learn from large datasets, making them more adept at identifying complex patterns. This results in better detection of sophisticated attacks.
Q2: What is the role of GANs in balancing datasets for IDS?
GANs create realistic synthetic samples that augment the minority class of attack data, enhancing the model’s ability to generalize and effectively recognize new attack scenarios.
Q3: What common mistakes should be avoided when implementing an IDS?
Avoid overfitting models by ensuring diversity in your training data and continuously updating your datasets to reflect current threat landscapes.
Q4: What tools are recommended for developing an advanced IDS?
Tools like TensorFlow, Keras, and Wireshark are recommended, as they facilitate deep learning model development and network traffic analysis, which are crucial for effective IDS implementations.