Revolutionizing Course Recommendations and Certificate Issuance with Deep Certifier-DX509
In a world increasingly driven by data and technology, the education sector is experiencing a paradigm shift. The integration of deep learning and blockchain technology is spearheading this transformation, particularly through innovations such as the Deep Certifier-DX509. This advanced model focuses on a dual pathway: developing an intelligent course recommendation system and a secure certificate issuance framework. Let’s dive deeper into its functionality, phases, and unique features.
Overview of the Deep Certifier-DX509 Model
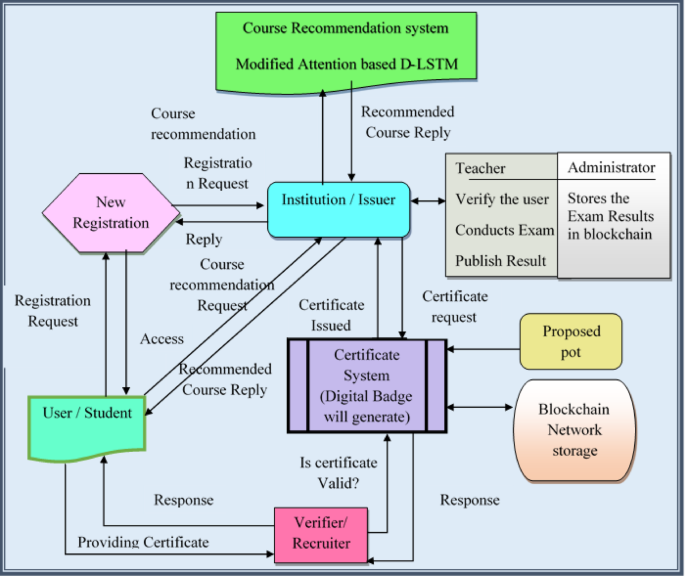
The Deep Certifier-DX509 operates through a well-structured four-phase process designed to maximize both user engagement and educational integrity. The system prioritizes user authentication, personalized learning experiences, and secure credential issuance, ensuring each participant’s achievements are accurately reflected and verifiable.
Phase One: Registration
The journey begins with user registration. Prospective students submit their profiles to the educational institution. Once their request is accepted, they are assigned a unique username and password, which they use to log in to the platform. Registration captures essential details, such as name, age, address, gender, and prior academic performance, all of which are vital for effective course recommendations.
Mathematically, the number of users ( K ) can be represented as:
[
K = { K_1, K_2, K_3, \ldots, K_r }
]
where ( K_r ) signifies the total number of users, and ( K_b ) points to an individual user in the dataset.
The academic data is encrypted via the Rivest-Shamir-Adleman (RSA) algorithm, ensuring maximum security. This encryption and digital signature process guarantees the confidentiality and integrity of the user’s sensitive information.
Phase Two: Login
Upon successful registration, users log into the platform, where they are greeted with personalized dashboards. For new users, the system drives them to register, cultivating an intuitive experience that enhances engagement from day one.
Phase Three: Course Recommendation via MA-DLSTM
Once logged in, users can seek course recommendations tailored to their academic history and interests. The Modified Attention-enabled Deep Long Short-Term Memory (MA-DLSTM) model is at the core of this phase. This model leverages both spatial and positional attention to analyze sequential data effectively, extracting critical patterns from a user’s past enrollment and performance.
The input data undergoes preprocessing, transforming it into a format compatible with the LSTM’s architecture. This intricate mechanism allows for the nuanced understanding of learning trajectories, drawing on learnings that span substantial timeframes.
An established equation underlines the functionality of the LSTM mechanism:
[
f_{ri} = \sigma\left( W{fr} \cdot [hid_{i-1}, D(Kb)] + B{fr} \right)
]
This produces detailed outputs, enriching the recommendation process with significant contextual information.
Phase Four: Examination and Certification
With a course assigned, users are paired with instructors who guide their learning journey. After completing the course, students undergo an examination, and their performance is assessed against a historical student performance dataset. Successful candidates can then request their certificates.
The certificate issuance system, utilizing the X.509 standard, confirms the validity of the scores through a powerful proof-of-work mechanism. Certificates are unique, confirming the authenticity of the user’s achievements and securely stored on a blockchain for future verification.
Learning Management System Interactions
Central to the educational ecosystem is the learning management system that bridges communication between students, instructors, and administrators. Once a student is enrolled in a recommended course, the institution keeps detailed records, inclusive of the user’s performance metrics.
During the examination, administrative integrity is maintained through rigorous roll number verifications. Post-assessment, results are recorded in the blockchain, fortifying the sense of authenticity surrounding the credentials earned.
The Certificate Sub-System: X.509 in Action
The certificate sub-system plays a pivotal role in authenticating achievements. The use of X.509 digital certificates brings a high level of security and reliability. These certificates not only include essential identifying features but also carry cryptographic signatures that validate their authenticity.
The implementation of a blockchain model, integrated with proof-of-work (PoW) consensus, safeguards against unauthorized alterations, thereby securing students’ academic records from fraud.
The flexibility of the X.509 standard allows for customizations tailored to institutions’ requirements, adding layers of functionality to the educational certificates issued.
Concluding Thoughts
The Deep Certifier-DX509 system encapsulates the convergence of advanced machine learning and secure data practices in education. By combining personalized learning with transparent and secure certificate issuance, it addresses crucial issues surrounding academic integrity and tailored learning paths. This innovative approach not only enhances educational experiences for students but also provides institutions with reliable mechanisms to authenticate academic credentials in an increasingly digital world. As education evolves, embracing such technologies could define future academic landscapes.