A Comprehensive Framework for Botnet Detection in IoT: An In-Depth Exploration
Introduction
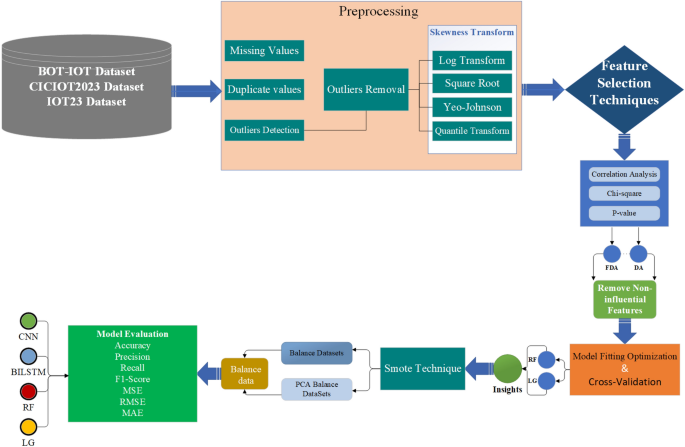
The rapid expansion of Internet of Things (IoT) devices has revolutionized connectivity but has also led to significant security challenges, particularly the threat of botnet attacks. Addressing these dangers necessitates advanced detection methodologies. Building upon identified limitations from previous research, this article elaborates on a holistic framework designed for botnet detection across three prominent datasets—BOT-IOT, CICIOT2023, and IOT23.
Methodology Overview
The proposed approach embraces a systematic methodology that integrates innovative preprocessing techniques, feature selection mechanisms, and ensemble modeling strategies. This comprehensive framework is structured to enhance the effectiveness of botnet detection, underscoring adaptability to diverse datasets with varying complexities.
Data Preprocessing and Quality Enhancement
Initial Data Handling
Data preprocessing is paramount; it involves filling in missing values, removing duplicates, and detecting outliers through the Interquartile Range (IQR) method. Initial cleaning efforts are crucial for ensuring the integrity of the datasets.
Advanced Skewness Reduction
To tackle skewed data—a frequent challenge in network traffic analysis—multiple transformation techniques (log transformation, square root transformation, Yeo-Johnson transformation, and quantile transformation) are employed. A comparative analysis facilitates the selection of the optimal transformation method to preserve key attack features, while reducing skewness. Insightfully, the quantile uniform transformation emerged as the most effective approach across all datasets.
Feature Selection Techniques
Statistical Analysis
Feature selection employs a combination of statistical methods, starting with correlation matrices to identify relationships between features. The analysis encompasses Chi-square statistics alongside p-value validation to discern feature significance across label classes. For instance, in BOT-IOT, 38 out of 46 features were selected, while in CICIOT2023, 42 out of 47 were identified as relevant.
Dependency and Distribution Analysis
Advanced techniques involve assessing feature distribution and proportional analysis, contributing to a nuanced understanding of feature dependency in relation to specific attack types. Features demonstrating minimal influence based on these analyses are eliminated, enhancing computational efficiency.
Model Optimization Framework
Classifiers Employed
The framework leverages Random Forest and Logistic Regression models, carefully optimized through threshold-based decision-making. Cross-validation reveals distinct characteristics among datasets—BOT-IOT and CICIOT2023 exhibit clear classification structures, whereas IOT23 presents a more intricate landscape. These observations emphasize the importance of understanding class imbalances in achieving robust detection.
Addressing Class Imbalance
To tackle the issue of class imbalance—a common occurrence in security datasets—the Synthetic Minority Over-sampling Technique (SMOTE) is implemented. This innovative approach enhances the representation of minority classes, while detailed analysis of class distribution ensures that performance is not compromised.
Evaluation Metrics
A rich array of performance metrics is employed to validate model efficacy. Conventional metrics include accuracy, precision, recall, and F1 Score, alongside regression metrics such as Mean Squared Error (MSE) and Root Mean Squared Error (RMSE). This comprehensive evaluation framework provides insights into model behavior across varied attack conditions, ensuring the practicality of the proposed methodology.
Datasets Characteristics
BOT-IOT Dataset
The BOT-IOT dataset comprises a wealth of network traffic data captured in real-world conditions, characterized by 72 million records, including multiple attack types such as DDoS and Information Theft. With processing, a reduced subset of 5% retains the essential features, enhancing the focus on critical security patterns.
CICIOT2023 Dataset
Launched in 2023, CICIOT2023 introduces a dynamic representation of IoT security contexts, boasting over 30 million traffic instances derived from a simulated IoT environment. This dataset includes an array of attack types and facilitates a robust understanding of real-time vulnerabilities.
IOT23 Dataset
This dataset offers extensive coverage of IoT network traffic, compiled from 23 distinct scenarios involving both Windows and Linux operating systems. Featuring diverse attack patterns, IOT23 provides a practical glimpse into the challenges faced by IoT devices today.
Handling Preprocessing Challenges
Across the datasets, challenges arise in handling missing values, measurement inconsistencies, and outlier management. Utilizing advanced methods for skewness handling ensures that transformations maintain the inherent signature of attack patterns, which is critical for accurate detection.
Advantages of Quantile Uniform Transformation
Quantile uniform transformation stands out for its compelling performance in preserving critical attack features while facilitating improved accuracy across models. Comparative analyses exhibit that this method is particularly effective at mitigating issues associated with skewed distributions, thereby enhancing the overall model performance.
Robust Feature Selection Methodology
A layered statistical approach enables a thorough examination of features across all datasets. The multi-faceted methodology promotes computational efficiency while retaining significant features, crucial for enhancing the robustness of detection.
Model Fitting and Validation
The ensemble framework encompasses detailed procedures for model fitting and validation, aimed at preventing both underfitting and overfitting. Utilizing a multi-model approach fosters resilience against varying behaviors observed across datasets, contributing to enhanced detection accuracy.
Class Balancing Initiatives
Adopting effective class balancing strategies, the methodology includes the application of SMOTE to produce synthetic minority samples. This dynamic approach not only enhances model robustness but also facilitates better performance across diverse datasets.
Performance Evaluation Framework
The evaluation framework systematically assesses both classification and regression performance, providing a nuanced perspective on the detection capabilities of the proposed methodology. By incorporating computational metrics, the framework further underscores the practical applicability of the models in real-world scenarios.
Conclusion
The holistic methodology presented for botnet detection across multiple IoT datasets illustrates the intricate interplay between preprocessing, feature selection, and model optimization. By emphasizing adaptability and robustness, this framework paves the way for enhanced security in increasingly vulnerable IoT environments.